- Home
- Learn
- Healthcare
- What is PHI? Best practices for securing patient health information
HEALTHCARE
What is PHI? Best practices for securing patient health information
Contents
When you visit a doctor or even fill out a health form online, you’re sharing some of the most personal details about your life. Things like your medical history, test results, or insurance information are not just data points. They are deeply private pieces of who you are.
That’s why protecting patient health information matters so much.
At a basic level, it comes down to trust. Patients expect the information they share with healthcare providers to stay confidential and be used only to support their care. When that trust is broken through data leaks or careless handling, the consequences can be serious. People may hesitate to seek care, withhold important details, or lose confidence in the healthcare system altogether.
There is also a legal and operational side to this. Healthcare organizations are required to follow strict privacy and security regulations designed to protect patient data. Data breaches can lead to hefty fines, legal trouble, and long-term damage to an organization’s reputation.
At the center of all these privacy and security efforts in healthcare is a concept known as Protected Health Information, or PHI.
Understanding what PHI is and how it should be protected is essential for anyone involved in healthcare.
So, in this article, we will break down what PHI is, explore why securing it is critical, and outline practical best practices for protecting patient health information in today’s healthcare environment.
PHI stands for Protected Health Information. In simple terms, it refers to any health-related information that can be linked back to a specific person.
Think of PHI as two pieces coming together. One is health information, such as a diagnosis, a lab result, or details about treatment. The other is identifying information, such as a name, phone number, email address, or even a photo. When these two are connected, the information becomes PHI.
The term PHI comes from healthcare privacy laws, most notably the Health Insurance Portability and Accountability Act, or HIPAA, in the United States.
Similar concepts exist in other countries as well, even if they use different names. The goal is the same everywhere. Patient health information should be handled carefully and protected from misuse or exposure.
PHI covers a wide range of information.
Some common examples include:
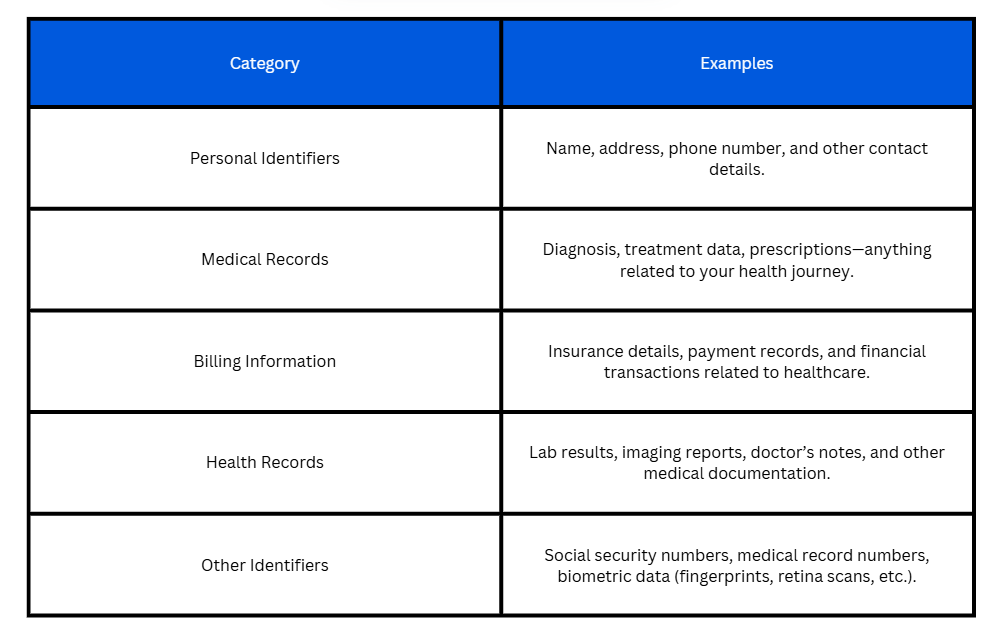
PHI does not only exist in hospitals or clinics. It can show up in emails, spreadsheets, healthcare CRMs, patient portals, and even handwritten notes.
It is also important to understand what does not count as PHI. If health information has been de-identified, meaning all details that could link it to a specific person are removed, it is no longer considered PHI. For example, a report showing average recovery times for patients without names or identifiers is not PHI.
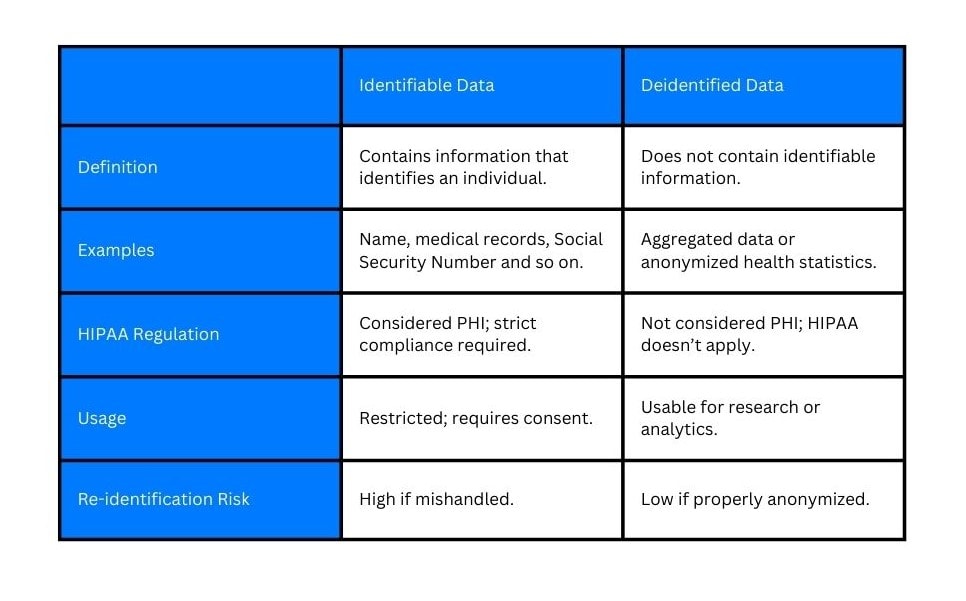
In short, if you can reasonably figure out who the information belongs to and it relates to their health or care, it should be treated as PHI.

Protecting PHI is not just the responsibility of doctors and hospitals. In fact, many different organizations handle patient health information and are required to keep it secure.
In the United States, HIPAA defines a group called covered entities. This includes healthcare providers such as hospitals, clinics, physicians, and labs. It also includes health insurance companies and healthcare clearinghouses that process medical and billing data.
Beyond that, there are business associates. These are third parties that handle PHI on behalf of covered entities. Examples include billing services, IT providers, cloud platforms, analytics tools, and healthcare software vendors. If an organization can access or store PHI as part of its work, it shares responsibility for protecting that information.
While HIPAA is specific to the United States, patient data protection is a global concern. Other regions have their own laws with similar goals.
For example, the European Union enforces the General Data Protection Regulation, or GDPR, which covers health data as a special category of sensitive information. Countries like Canada, Australia, and India also have healthcare privacy and data protection frameworks.
Although the details differ, the underlying principle is the same everywhere. Organizations must limit access to patient data, protect it from unauthorized use, and respect individuals’ privacy.

One of the most straightforward reasons PHI security matters is that it is required by law. In the United States, regulations like HIPAA set clear rules for how patient health information must be collected, stored, shared, and protected.
Non-compliance can result in large financial fines, legal action, and mandatory corrective measures. In some cases, violations can even lead to criminal charges. Simply put, protecting PHI is a basic requirement for operating in the healthcare space.
Beyond legal obligations, PHI security is fundamentally about doing the right thing.
Patients share health information with the expectation that it will be kept private. They trust healthcare providers with details they may not even share with family or friends.
When that trust is broken, it can damage patient relationships and make individuals reluctant to share information that is critical for their care.
One of the most immediate risks is identity theft and fraud. Stolen health information can be used to file fake insurance claims, obtain medical services under someone else’s name, or even commit financial fraud. For patients, fixing these issues can take months or even years.
As we touched on, organizations can also face significant fallout. Data breaches often trigger investigations and regulatory scrutiny. Fines for violations can be substantial, especially if negligence or repeated failures are involved. Beyond financial penalties, organizations may be required to overhaul systems and processes under tight deadlines, adding operational strain.
Reputation damage is another major consequence. Trust once lost is difficult to rebuild. Patients may choose to take their care elsewhere, and public confidence can decline quickly after a breach becomes public.
Perhaps most importantly, poor PHI security can disrupt care itself. If systems are compromised or taken offline due to security incidents, providers may lose access to critical patient information when they need it most. This can delay treatment and increase the risk of medical errors.

Administrative safeguards focus less on technology and more on how people, processes, and policies work together to protect patient information. Without strong administrative controls, even the most secure systems can fail.
A good starting point for protecting PHI is understanding where the risks are. Risk assessments help organizations identify how patient data is collected, stored, accessed, and shared across systems. This includes everything from electronic health records and emails to spreadsheets and third-party tools.
The goal is to spot weak points before they turn into problems. For example, are employees sharing data through unsecured channels? Are outdated systems still in use? Once such risks are identified, policies can be put in place to define how PHI should be handled in everyday situations.
Even with strong policies, PHI security can break down if people are not properly trained. Employees are often the first line of defense. Regular training helps staff recognize phishing emails, understand secure ways to handle patient data, and avoid common mistakes like sharing information unnecessarily.
Ongoing training helps keep privacy and security top of mind as threats and technologies evolve.
No system is completely risk-free. That is why having an incident response plan is critical. This plan outlines exactly what steps to take if PHI is compromised, including how to contain the issue, notify affected parties, and meet legal reporting requirements. Clear planning helps organizations respond quickly and responsibly.
Technical safeguards protect PHI at the system level, ensuring only authorized people can access sensitive data and that it stays secure while in use or storage.
Controlling who can see and use PHI is essential. Access controls limit data exposure by giving users only the permissions they need. For example, a billing specialist may access payment records but not detailed clinical notes, while a physician needs clinical data but not administrative files. Role-based access simplifies management and reduces the risk of unauthorized exposure. Regularly reviewing and updating roles is crucial when staff change positions or leave.
Authentication verifies that users are who they claim to be. Passwords alone are no longer sufficient. Multi-factor authentication (MFA) adds extra verification steps, like a code sent to a phone or a biometric scan. MFA greatly reduces the risk of unauthorized access even if passwords are compromised.
Encryption protects PHI by converting readable data into a coded format that only authorized users can unlock. It is critical for both data in transit, such as information sent from a patient portal to a provider, and data at rest, like PHI stored on servers or backup systems. Even if someone gains access to these systems, encrypted data remains unreadable without the correct keys. Encryption also supports compliance with privacy regulations and helps safeguard patient trust.
Even with strong access controls and encryption, it is important to continuously track how PHI is being used. Monitoring systems record user activity and create audit logs, which can reveal unusual patterns or unauthorized access.
For example, an electronic health record (EHR) system like Epic or Cerner can track who accesses each patient’s record, what changes are made, and when.
If someone suddenly tries to access a large volume of patient records outside their normal workflow, the system can trigger alerts, helping detect potential breaches early. Regular audits of these logs ensure compliance with policies and regulations while helping organizations spot weaknesses before they become serious problems.
Keeping software and systems up to date is another critical safeguard. Many security incidents occur because organizations use outdated software with known vulnerabilities. Routine patching and updates fix these vulnerabilities and improve system defenses against new threats. This applies to electronic health records, patient portals, healthcare CRMs, mobile devices, and any other system storing or accessing PHI.
Physical safeguards are about protecting the places and devices where patient health information (PHI) lives.
One of the first steps is controlling physical access to areas where PHI is stored or processed. This includes server rooms, offices, filing cabinets, and workstations. Simple measures like locked doors, access badges, keycards, and security cameras help limit entry to authorized personnel only.
For example, only IT staff might have access to the server room, while clinical staff access patient records in their own work areas. Visitors and non‑clinical staff should not be able to enter sensitive areas without supervision.
Devices that access PHI, such as desktop computers, laptops, or external drives, should be kept secure when not in use. This includes locking screens when stepping away and storing devices in secure locations after hours. Also, if an equipment is no longer needed, it should be wiped clean or destroyed so data cannot be recovered.
Physical safeguards also extend to paper records and printed documents. Many healthcare organizations still use printed forms. Policies should be in place for how paper PHI is handled, stored, and disposed of.
Shredders, locked file cabinets, and clear instructions for printing and retrieving documents reduce the chance that sensitive information is left out in the open.
Protecting patient health information does not stop at an organization’s own walls. Many healthcare providers and systems rely on outside companies to help with billing, cloud storage, IT support, analytics, and other services. When these third parties have access to PHI, organizations must actively manage these relationships to make sure patient data stays secure.
Before a vendor is allowed to handle PHI, healthcare organizations should assess how that vendor protects sensitive data.
This includes checking if the vendor has clear protocols for data handling and a track record of compliance with privacy standards. Periodic reviews and continuous monitoring ensure that they maintain these protections over time.
Under HIPAA, a business associate agreement (BAA) is often required before any third party can access or store PHI on behalf of a healthcare organization. A BAA is a legally binding contract that defines how PHI will be used and protected and what must happen in case of a data breach. These contracts also require the vendor to follow HIPAA’s privacy and security requirements and to notify the healthcare organization if any unauthorized access or breaches occur. Having a BAA in place helps both parties avoid legal penalties or liability if PHI is mishandled.
Healthcare CRM systems, such as LeadSquared, can play a meaningful role in supporting PHI‑aware workflows in ways that align with privacy and security standards.
These systems act as centralized platforms for organizing patient data and interactions.
One of the key ways CRM tools support PHI security is through secure communication channels. Unlike standard email or messaging apps, secure communication features built into healthcare CRM platforms ensure that messages containing sensitive details remain protected while being shared among authorized users. This is especially important for handling appointment reminders, follow‑ups, and coordinated care messaging.
Another important capability is permission controls. CRM systems can assign access rights based on a user’s role within the organization, so only those who need to see specific patient information can do so. This approach limits unnecessary exposure of PHI across teams and helps enforce the principle of least privilege.
Healthcare CRM tools also keep audit logs and activity records of who accessed or modified PHI and when. These logs are valuable for both internal oversight and regulatory compliance. They allow organizations to trace unusual activity and demonstrate accountability during audits.
Finally, CRM systems that work with PHI typically require a business associate agreement (BAA) with the provider using them. A BAA clarifies responsibilities and ensures that both parties understand their obligations in protecting patient data under applicable regulations.
Used thoughtfully within the context of broader privacy and security practices, healthcare CRM and similar digital tools can support your healthcare workflows without putting PHI at risk.
If you’d like to better understand how a healthcare CRM like LeadSquared supports PHI-aware workflows, feel free to book a quick demo.
Healthcare staff sometimes access PHI on personal phones, tablets, or laptops. Covered entities are responsible for ensuring that any device that stores or transmits PHI is secure. Policies should enforce encryption, strong passwords, and secure apps. Even when staff use personal devices, the organization must maintain HIPAA compliance and can require mobile device management or secure VPNs to protect PHI.
PHI should only be shared on HIPAA-compliant systems. Using unsecured email, messaging apps, or public platforms can violate privacy rules. Organizations must provide staff with secure channels for handling PHI, such as encrypted messaging within an EHR or CRM system, and ensure that employees are trained to use these channels correctly.
PHI is any health information that can identify a patient and relates to their health, care, or payment. This includes names, addresses, medical records, diagnoses, billing information, and insurance details. Even metadata like phone numbers or emails linked to patient care counts as PHI. Staff should treat all such data according to organizational privacy and security policies.
For treatment, payment, and healthcare operations, HIPAA does not require patient consent for PHI sharing within the organization or with authorized business associates. However, organizations must maintain policies explaining how PHI is used and ensure that access is limited to those who need it. Consent may be required for other purposes, such as marketing or research.
A breach occurs when PHI is accessed, used, or disclosed in an unauthorized way that compromises its privacy or security. Covered entities must investigate potential breaches, determine if they meet the breach definition, and follow regulatory requirements for notification, mitigation, and documentation. Routine audits, monitoring, and staff training help prevent breaches and prepare the organization to respond quickly if they occur.
The HIPAA Privacy Rule sets national standards for how protected health information (PHI) can be used and disclosed by covered entities and their business associates. It applies to PHI in all formats — electronic, paper, or oral. The rule governs who may access and share PHI, requires policies for permitted uses and disclosures, and gives patients rights such as access to their records and the ability to request corrections. Organizations must implement reasonable safeguards to protect PHI and comply with patient rights and disclosure rules.
The Security Rule focuses specifically on electronic PHI, meaning PHI that is created, received, maintained, or transmitted in electronic form. It requires covered entities to implement administrative, physical, and technical safeguards that ensure the confidentiality, integrity, and availability of ePHI. These safeguards must be tailored to the organization’s size, risk environment, and technology. Conducting risk analyses and regularly updating security measures are also required.
The Privacy Rule applies to PHI in all forms (electronic, paper, oral) and focuses on how PHI may be used or disclosed and patient rights. The Security Rule applies only to electronic PHI (ePHI) and focuses on how that information should be secured through specific safeguards — administrative, physical, and technical — to prevent unauthorized access or use. Together, the rules complement each other in comprehensive PHI protection.
To meet the Security Rule, covered entities must:
Ensure ePHI remains confidential, intact, and available to authorized users;
Identify and protect against threats to ePHI security or integrity;
Prevent impermissible uses or disclosures of ePHI; and
Implement safeguards that are reasonable and appropriate to their operational context based on risk analysis.
Yes. Both the Privacy and Security Rules require covered entities to ensure workforce compliance. This includes training staff on PHI and ePHI handling policies, monitoring access and use, and enforcing disciplinary policies for non‑compliance. Covered entities must make sure everyone in the workforce understands and follows the required safeguards and policies.
8
1